Do different questions come to your mind that how hackers hack email and passwords? Or do you ever want to know how you can hack into someone’s email account? When we first think about this, it almost seems impossible as you know that using a strong password, enabling 2-factor authentications and following some essential security checklists will probably make your email account immune to penetration.
If still, it is possible to hack, then you must know that hacking is challenging to do it is a very challenging job for an average person who does not have any knowledge related to computer security. This article explains how to hack email password 2022 in a step-by-step fashion.
Still, is it that easy and straightforward? The answer is NO; if you have planned your attack cleverly then even the most informed user shall fall for it. Email hacking requires creativity and yet most importantly, PATIENCE, apart from the basic knowledge of computer security.
Keep in mind that for most of the part whenever an email account gets hacked its due to your ignorance and not due to the involvement of an email service provider. Believe it or not, but truth has been told.
Contents
Top 3 Best Ways on How to Hack Email Addresses in 2022
Today almost all of us regularly use the Google email service and many of us access emails on a smartphone via the Gmail application. The decade-old phishing attacks are not seen active these days due to keen security awareness and features of email providers like Ip whitelisting, 2-factor authentication and many others. It is however not possible to hack username and password unless and until you carry out a highly sophisticated phishing attack that can bypass the SMS 2FA
So if you want to get into someone’s Gmail account is not an easy job as we have to take control of their smartphone. One way to do that is that you install a “spy application” on their smartphone and as a result, it will record all the activities they carry out on their phone, and yes that includes typed passwords as well. Isn’t that amazing??
You will find many ways all over the internet on how to hack email passwords, but we bring for you among the best and easy ways to do so.
READ ALSO: How to Send Secure and Encrypted Emails – Most Secure Email 2022.
Hack an Email Account Password using Spying Apps
We have explained the basic idea of a spy app that is a code that once installed on the target device records all the activity of the user like calling, social media activities and much more.
This is the most widely used way by hackers to steal the victim’s private data like email passwords and credit card details. You need to convince the victim to install a spy application by any means on their phone if you do not have access to their phone.
How to spy on smartphones using special applications:
Now hacking into someone’s email account does require you to know or change their passwords. In spite of this, you can get in, peak into their account, read all the received and sent emails, etc. Just do what you want without the need to reset passwords.
The best part of the spy application is that it lets you hack into someone’s email without their password. The spy application highly recommended is the mSpy. Now, this instead of hacking also enables you to log phone calls, spy on text messages, Monitoring WhatsApp, log passwords and much more. You can also read our guide on how to hack a WhatsApp account. Best of all it is compatible with iPhone and Android. Now below is hot mSpy works for you:
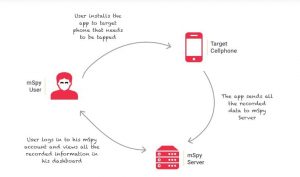
One of the biggest challenges that you will face is installing this app in your victim’s smartphone. It is much easier to get this application installed on your spouse’s phone than your friend’s phone. You would need to learn and know a few skills related to social engineering that will let you get a hold of people’s smartphones.
You can install it remotely on your victim’s smartphone as long as you trick them into installing it. As soon as the application gets installed, it runs very smoothly, in a stealth mode that can monitor all the activities as well as capture keystrokes, including email passwords.
READ ALSO: How to Secure Your Gmail Account 2022 – Email Security Guide.
How to Spy on Desktop Computers using Software:
The spy application for desktop computer systems will only work in the presence of anti-malware or anti-virus applications. You can also use keyloggers for windows machines when your anti-virus is turned off.
If you can physically access your victim’s computer system like you want to monitor your home computer system to spy on your spouse or children, then all you can do is get yourself a hardware-based keylogger. It is a USB device that can be inserted between the computer system and keyboard to capture all the data that the victim enters.
The keystrokes are then collected in a temporary file and then stored in a flash memory that can be accessed later over Wi-Fi or by connecting it to your computer system.
The hardware that has been displayed in the above picture is the PS2 keyboard compatible keyboard. These days we mostly use USB keyboards in our offices and homes. But with the advancement in technology in these hardware keyloggers enables them to communicate with its owner for an exchange of logged data.
With the help of an in-built wi-fi chip, you can pick up quickly all the information that carries passwords, credit card details or anything else that gets typed in on the keyboard over the air. If you want, then the keylogger can be shifted to any computer system for retrieving data.
Some tips to stay safe from such mishaps
- You must never click on the suspicious links
- You must never install any Software patch or any Keygen, unless and until you download it from a legit site.
READ ALSO: The Best Hacking Books – Learn Hacking Quickly.
Brute Forcing Email Account Passwords or Guessing them
Password guessing or resetting is a type of social engineering technique that deals in with manipulating someone’s mindset with the purpose to find out his or her personal information. But for this, you need to possess excellent thinking power along with social skills.
Hackers, most of the time, know the victim very well. The hacker can be your boyfriend, girlfriend or even a family member. He can also be your online friend with whom you share your details like cell phone number, date of birth and other things like music, movies or anything else.
All this information gets enough for a hacker to start guessing for your password or security question of the email account and also reset the password and his own and login into your account. There is a high chance for him to guess in your security question and provide with the answer.
READ ALSO: How to Hack Any SQL Database Password – Cracking SQL Passwords.
Hacking Email Accounts using New Phishing Techniques
Phishing is considered a criminal process which is an attempt to steal private and sensitive information like passwords, usernames, and credit card details by disguising as a trustworthy website. Phishing is the most widely used social engineering technique for hacking email just because it is super affordable and easy to execute.
This is the simplest way in which you can trick someone into providing you with their login details or private information. Even highlight educated IT professionals can fall for it.
It can be both carried out by email or through instant messengers. If often misguides people to enter details at a deceptive website that looks and feels almost like the real one.
To hack the Gmail account, the hacker might send you an email that carries a link to the fake login page of Google that appears to have come from the Google team. It requests you to change the password or update any personal information. He can also create an online persona of your cow-worker or boss and send you an email invite for editing documents on Google drive or participate in Google Hangout calls.
If by any chance you fall prey to this and enter all your login credentials in the fake login page then all these details are sent to the hacker’s server at the time you will be redirected towards to the main page of your email dashboard or account.
READ ALSO: How to DDoS Like a Hacker – DoS PC, IP Address or Server.
2-Factor Authentication is not Enough
Attackers can defeat some forms of two-factor authentication with the purpose to steal credentials and maintain access to victims’ accounts. Scammers today even use a phishing attack to loot their victims. They usually sent in their phishing emails that appear as if they come from a bank or a credit company thus requesting verification of details.
Now let us have a look at the phishing email set up for hacking an Apple ID:
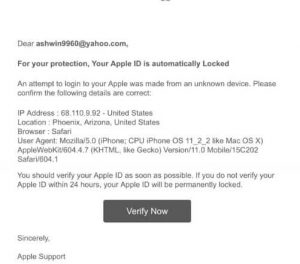
The success rate of this process is about 70-90% as it depends upon the user who is bound to make a mistake and log in to the phishing site.
READ ALSO: How to Hack and Cheat in Flash Games.
UPDATE: A recent vulnerability in Gmail allowed attackers and spammers to bypass protections. This flaw allowed them to skip the SPF and DMARC checks. This meant that Spam was actually passing through and it also caused a major outage across their services in Google Drive.
Recommended articles to read:
- How to Hack an Instagram Account – Securing an Insta Account.
- How to Hack a Twitter Account – Secure Twitter Account from Hacking.
- How to Track & Trace an IP Address and Its location.
Is your Email Account Secure?
This article includes everything you need to hack email password 2022. We have detailed various methods for hacking into Gmail, Outlook, Yahoo, and various other providers.
NOTE: This is a security guide showing you the methods that can be USED to hack your account. These are not actual guidelines, and we are not held responsible for any damages you may cause. This is only for educational purposes.







Great read, just shows how powerful the phishing attach is even today.
Can a hacked email address help hack a facebook account?
It depends if there are any linked FB accounts with that address.
Hi
The spy app you are mentioning about, how can we install it in the targeted phone without knowing them or once it is installed, will it appear as an app in the phone.
Is there a way where we can just send the link to the person whose mobile we need to hack and the app gets installed automatically with one click.
Thanks
Tried it on my iPhone and works.