
BlackShades is a malicious Trojan horse that is used by hackers to control infected systems remotely. It targets the systems using OS based on Microsoft windows. More than 5 lakh computer systems have been affected by this worldwide according to US officials.
Many people were arrested back in 2014 by the FBI who had BlackShades RAT download installed in their system. Before the crackdown, these were sold for around $40 on hack forms and generated $350,000.00 in sales according to a report.
Contents
How BlackShades RAT Works
It infects the system by getting download on the victim’s system whenever he/she accesses a malicious webpage and also by any external storage devices like USB flash drivers.
It can infect different computer systems from the release of a bait that hackers can make use of.
When hacking organizations such as OffensiveEncode and Cyber-Sec decided to develop unique features for coupling the software like DDoS/ TCP Flood, un-detectability and backdoor persistence features, an improved version of this got released after the release of the first version.
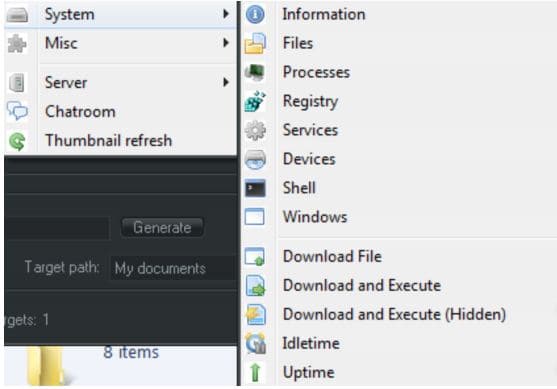
These are used remotely to access an infected system without any authorization. It allows hackers to perform various actions on the infected system without permission.
Includes the ability to:
- It can access and modify files on a victim’s PC.
- It can log keystrokes on the victim’s PC.
- Have access to the webcam.
- Use the affected system as a proxy server.
- It can download as well as execute files on the victim’s system.
- It can include the victim’s system in a botnet; this allows the hacker to perform denial-of-service attacks on it.
It can be used by the hackers who even have little experience or by the script kiddies, hackers that used the programs that are developed by others to attack PCs.
Now, these can also act like ransomware. This is used by hackers to restrict access to the victim’s system and demand a ransom paid to the hacker for the restriction to be lifted.
SEE ALSO: Download DarkComet RAT Full Version.
BlackShades RAT Features (Refreshed)
Its toolkit provides with a malicious actor along with a plethora of powerful remote access capabilities to control the victims. When a victim gets infected, the level of compromise gets quite high. The capabilities include:
- System administration and modification.
- System infection.
- Networking control and data exfiltration.
- Features that can be used for monetary gain.
- Process enumeration.
- Access to the window registry.
If these go in the wrong hands, they can cause irreversible damage to a compromised system. Malicious actors can collect the same information regarding the remote system as if they had physical access to the machine.
Moreover, the malicious actors also can download remote executables and then run them on the infected machine. This can be dangerous, allowing the malicious actor to propagate other malware like:
- Dirt Jumper DDoS Toolkit called Drive, a great alternative to LOIC.
- Zeus Crimeware Toolkit.
It has gained a lot of popularity due to its surveillance features. The media have reported that it has been used against Miss Teen USA and also by the government entities during the civil unrest.
- With this, hackers can monitor video as well as audio data of the infected victims.
- They can record essential logging information from the users providing them with access to sensitive credentials for banking, personal sites, email and other web-based apps.
Live loggers, a keylogging feature that provides cyber-criminal with some real-time logging data regarding the victim including:
- When data is being inputted.
- Victim’s local time of the day.
All the details provide the criminal context, whereas the other information is being used and for what purpose.
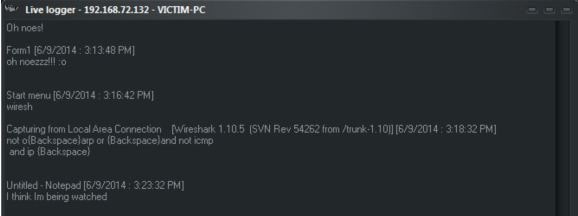
Blackshades RAT provides users with the ability to capture the screen of the infected victim. This allows the attackers to watch everything that the user is doing at the moment. This one mimics the capabilities of legitimate software like TeamViewer that comes with the advantage that the victim does not know that information is being shared.
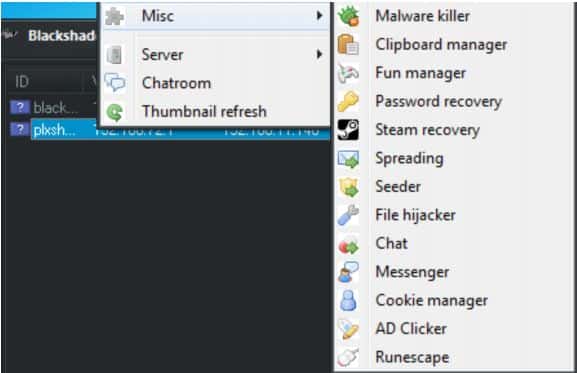
It also provides it, users, with some other features as well:
- Fun manager; It allows the malicious action to randomize a user’s mouse or display a message box to an infected victim.
- Malware Killer Option; It cleans the system of the infected payload though this feature was ineffective in our very own lab tests.
SEE ALSO: Download QuasarRAT For Windows 10.
How to Detect and Remove BlackShades
It can be removed and detected with the help of different anti-virus programs. However, hackers use this software to avoid detection of its infections by using software that obfuscates the blackshades binary to prevent exposure by anti-virus programs, which the organisation also sold along with its software. Alternatively, you can also run a full system scan with Malwarebytes and that will also get this rootkit away for you.
Why Using BlackShades is Dangerous
Citizen Lab and EFE reported on it as it planned to target the opposition forces in Syria back in 2012.
Then in 2015, Stefan Rigo from Leeds was given 40 weeks suspended sentence as he used it against 14 people, in these seven were those who he knew personally. It was later revealed that he paid for the software by using his ex-girlfriend’s payment card.
The FBI Crackdown that was a major operation
A sting operation started back in 2012 by FBI known as Operation Card Shop. With this, 24 hackers were arrested from 8 different countries. One of the men who got arrested was Michael Hogue, who is known as xVisceral in the world of online hacking communities. He is the co-creator of this got arrested and indicted charges under 18 U.S.C. He was sentenced to 5 years of probation with 20 years suspended prison sentence.
Then in 2014, another operation was started worldwide to combat its use which helped to arrest more than 100 people from 10 different countries.
On May 19, against five individual some charges were imposed in the US; 2 men got identified as developers of blackshades and the other three were selling it or using it to infiltrate other people’s systems. As a part of the operation, around 359 searches were made, and more than 1100 devices were seized. Moreover, according to the FBI, over five hundred thousand, computer systems in more than 100 countries were infected by this malware.
Source: ABC News.
BlackShades Alternatives:
- Download Remcos RAT Free in Full Version.
- Download NanoCore RAT (Latest Release).
- Download njRAT Remote Administration Toolkit.
Disclaimer: Please use this tool at your own risk. We have provided it only for educational and informational purposes. SecuredYou will not be held responsible for any damages caused by you using this RAT software.
BlackShades RAT Download – #1 Remote Hacking Tool
Today we have unveiled a dangerous yet useful remote administration tool known as BlackShades RAT download. Do let us know if you have any particular preferences or if you would also like to see a post about Plasma-RAT?
Note: The code for this tool was picked up from its official Github page.







is this 5.5.1?
Yep that is correct.
Is this any better in comparison to Orcus or not?
Much more and less prone to being detected by an Antivirus.