Hydra which is also called as THC-Hydra is totally a command-line-based program that is used to decrypt passwords from a lot of applications and protocols with the help of the dictionary attack and wordlists. THC is basically the abbreviation for “The Hacker’s Choice” and this is also the name of the company which developed and manufactured this software.
You can now Download THC Hydra for Free! It is a corresponding login cracker that can be used to perform great attacks with numerous protocols. It is a very flexible and fast software in performance. People are also using Hydra to hack Facebook account passwords. The other quality of this tool is very useful and it is about the easy adding of the new modules.
Contents
What is THC Hydra?
The best thing about this software is that it is totally an English Language software and it can be used in almost every UNIX system and also on Windows through the help of the Cygwin environment. The latest version of this software is also the subject of GPL version 3 available within the software. Another great alternative to Hydra is John The Ripper which is also a password cracker tool but is far more advanced.
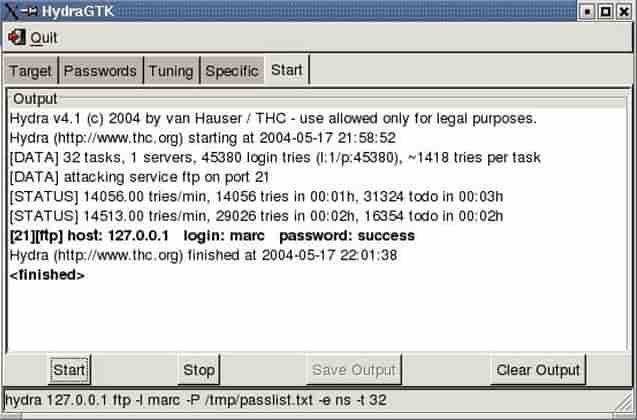
The most important and best thing that I found out in this software is that there are lots of other software that are used to decrypt passwords but none of them supports more than the one protocol which is used to support parallelized connects or perform the attack. Such tools are used in password guessing attacks, for example, trying to find the wifi password of a wireless network.
Supported Platforms and OS
Before we talk about the software in detail, let’s talk about the platforms that are supporting this password-cracking software. The list of those platforms or Operating systems (OS) is as follows:
- All of the UNIX platforms (including Linux, Solaris, *BSD, and of course Windows as well).
- macOS or Macintosh Operating System (OS) (Basically it is a BSD clone.)
- Microsoft Windows with the Cygwin (including both IPv4 and v6).
- All of the Mobile Phones Systems (MPS) that are based on Linux, QNX or MacOS (for example Android, iPhone, Blackberry 10, Zaurus, and iPaq also etc.)
Also read: DBAN Free Download.
Supported Ports Numbers
Now I am going to list the services that are supported by this password cracking software. These services make password cracking a lot easier than you can even imagine. The list is as follows:
- CISCO
- HTTP(S)
- Rexec
- SIP
- SMTP
- SMB(NT)
- NNTP
- MySQL
- IMAP
- Oracle
- SSH
- SOCKS
- Subversion
- Telnet
However, the module for all new services is very easy to use so it wouldn’t take a lot much time until all of the services are supported. This tool is totally proof for the concept code which is good to give the possibility of easiness to gain unauthorized access from remote to a system by researchers and consultants.
Read: DroidSQLi Free Download.
How to use THC Hydra Password Cracking Tool?
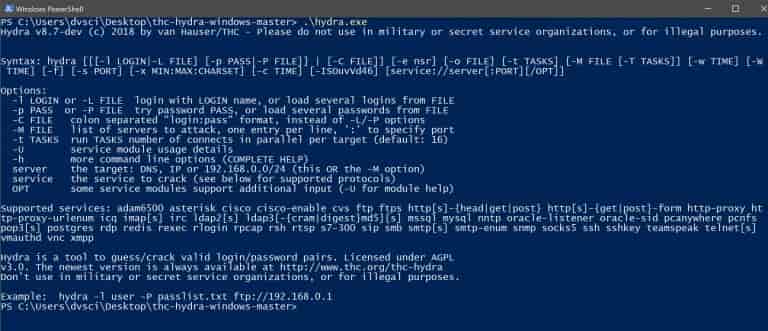
This software is very easy to use. If you enter “hydra” only a short summary of the very important options will available and displayed. And to see all the available command-line options you will have to enter “./hydra -h”.
Here is the syntax that can be used for entering the command line options within this password cracker:
“hydra [some command line options] [-s PORT] TARGET PROTOCOL [MODULE-OPTIONS]”
This software is totally command-line based so you will have to learn all of its commands to completely use this software. I recommend you watching a THC hydra tutorial on Youtube to get to know this great brute force tool.
You should use Rockyou.txt 2021 if you are not having much luck in hashing passwords. This is a gigantic wordlist formed from a combination of breaches that included credentials from LinkedIn, Gmail, and Snapchat.
Read: Wireshark Download For Windows.
Download THC Hydra Free Latest Version 2022
So, that was all the information about the THC-Hydra Password Cracking Software Free Download. In this guide, we learned about this software and we came to know about all of the basic information about this software. I would like to warn you that this guide was only for educational purposes and it shouldn’t be used to harm someone or harm that person’s property. I would also suggest you try the Metasploit Pro framework to learn more about various types of hacking and attach methods. It is very easy to install on all major OS including Windows, Linux, and Mac.
Disclaimer: Please use this tool at your own risk. We have only provided it for educational and informational purposes.
Version: 9.0 (Latest version as of January 2022).







This is great, I was looking for this for a long time and found it! Thanks
Very happy that it worked.
Hi shaheer can I get your help ?
Sure, how can I help you?
how do you configure it to work?
I downloaded it and I don’t know how to get it to start. I don’t see a application.
It should be on your desktop, a shortcut must be created run that.
I downloaded it but I have no idea where to type in
./configure
make
make install
Can you help me, please?
You have to type this in the terminal.