
Wifiphisher free download 2022 is a rogue access point framework that is used to conduct red team engagements for testing wifi-security.
- The penetration testers can achieve a man-in-the-middle position against all wireless clients by performing targeted wifi-association attacks.
- To mount victim-customized web phishing attacks against all the connected users with the purpose to capture credentials like from the third-party login pages or WPA or WPA2 pre-shared keys.
- To infect victim stations with malware.
Contents
Wifiphisher Features
- Powerful
It can run for a longer time like hours inside a Raspberry Pi device executing all the new wifi association techniques such as Evil Twin, Karma and Known Beacons.
- Modular
Users can write both complicated and straightforward modules in python to expand the functions of the tool or create custom phishing scenarios to carry out particular attacks that are target-oriented. If you don’t have it already installed, follow our python installation tutorial for Linux.
- Flexible
It can support many arguments and comes with a set of community-driven phishing templates for various deployment purposes.
- Easy to Use
It is both for beginners and advanced users. Advanced users can use the rich features, whereas beginners can start simply with “./securedyou/wifiphisher”. It carries quite a textual user interface that guides the tester throughout the process.
- Free
It comes in free, no payments required! Moreover, it carries full source code that user can study, change or even distribute under all the terms of GPLv3 license.
Now, attacks such as “Known Beacons” and “Lure 10” were disclosed by the developers, and this was the first tool to incorporate them. The best part about the machine is that a community of developers and users supports it.
SEE ALSO: Download Reaver WiFi WPS Pin Hacking Tool For Free.
How to Use Wifiphisher to Hack Wireless Access Points
- In the first step, it associated the wifi-clients unknowingly. It achieves this by adopting the following techniques, such as:
- Evil Twin: In herein creates a wireless network that is fake and looks just like a legitimate network.
- Karma: Here it masquerades in the form of a public network that is searched by wifi clients nearby.
- Known Beacons: It broadcasts a dictionary of common ESSIDs to which wireless stations have connected to in the past.
It keeps pm forging reauthenticate or disassociate packets at the same time to disrupt the available associations and then lure victims using the techniques mentioned above.
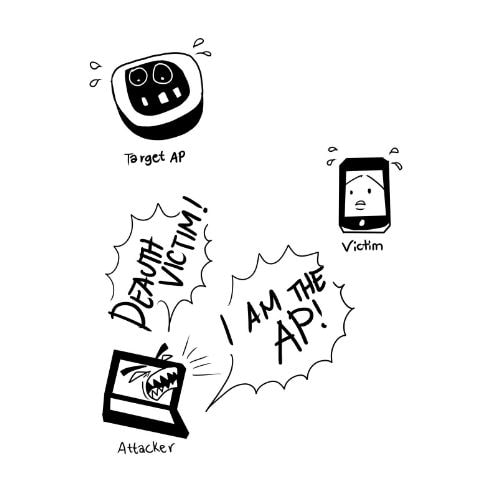
- Several attacks can be performed once it provides penetration tested with a man-in-the-middle position. Such as a tester might perform data sniffing or scanning the stations of the victims for vulnerabilities.
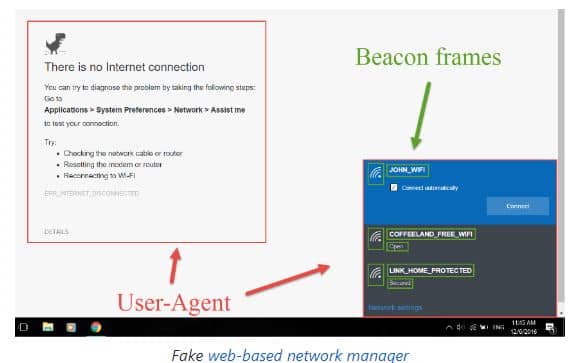
By using this, advanced web phishing techniques are entirely possible by gathering information there from the target environment and the victim. Like in our scene, this shall get all the info from broadcast beacon frames and the HTTP User-agent header to display a web-based imitation of windows network manager with the purpose to get the pre-shared key.
SEE ALSO: The 10 Best WiFi Hacking Tools for Linux that are free.
How to Install Wifiphisher
If you want to install the latest development, then use the following command:
Step 1: git clone https://github.com/wifiphisher/wifiphisher.git # Always get the newest build.
Step 2: cd wifiphisher – Change your directory to where it is installed.
Step 3: sudo python setup.py install # Install any dependencies.
As an alternate, from the releases page, users can also download the latest stable version.
Wifi Phishing- Usage
- From inside the tools directory, you need to run the tool by typing in python bin/wifiphisher.
- As you run it without any option, it shall be the correct interfaces and ask the other user to pick ESSID of the target network as well as phishing scenario to perform. The tool shall perform both Evil Twin and Karma attacks by default.
wifiphisher -aI wlan0 -jI wlan4 -p firmware-upgrade –handshake-capture handshake.pcap
- You can use wlan4 for DoS attacks and wlan0 to spawn the rogue access point. Then from the list, you need to select the target network manually and perform a firmware upgrade. To verify that the captured pre-shared key is correct. You can do this by checking it against the handshake in the handshake.pcap file.
The firmware upgrade scenario is thus an easy way to obtain PSK from a network that is protected by a password.
wifiphisher –essid CONFERENCE_WIFI -p plugin_update -pK securedyoutestpassword
- You need to pick up the correct interfaces automatically. Target the wifi with ESSID CONFERENCE_WIFI and then perform the plug-in update scenarios. A password shall protect evil twin with PSK s3cr3tp4ssw0rd.
It is quite useful against all the networks with disclosed PSKs like in conferences. The plug-in scenario provides with an easy way for the victims to download malicious executables like malware that carries a reverse shall payload.
wifiphisher –essid “SecuredYou Office WiFi“ -p oauth-login -kB
You just need to simply spawn an open wifi network with an ESSID wifi and then perform the Oauth Login scenarios. Moreover, you need to mount the known beacons wifi automatic association technique.
It is quite useful against victims in public areas as it provides a simple way to capture credentials from all the social networks like Facebook.
SEE ALSO: Download Fern WiFi Wireless Password Stealer.
Wifiphisher Commands List
- Maximum (-m) just choose the max number of clients to deauth. List of clients shall be emptied and then repopulated once you have hit the limit. Like –m 5
- No update (-n) do not clear the file as it reaches the max (-m) number of clients. Needs to be shown in conjunction with –m. Like -m -n
- Timeinterval (-t) choose the time interval between packets that are being sent. By default, it needs to be as fast as possible. If you see some Scapy errors such as “no buffer space” then you can try –t .00001
- Packets (-p) select number of packages that need to be sent in each deauth burst. 1; 1 is the default value, one packet to the client and one to the AP. Send to deauth packets to the client and 2 to the AP: -p 2
- Directedonly (-d) just skip the de-authentication packets to broadcast address on the access point and send to the client/AP pairs only.
- Accesspoint (-a) enter the MAC address of a particular access point to the target.
- Jamminginterface (-ji) choose an interface for jamming. By default, it shall find the most powerful interface and starts the monitor mode on it.
- Apinterface (-aI) choose an interface for a fake AP. By default, it shall find the second most potent interface and then starts monitor mode on it.
SEE ALSO: Download WiFiKILL App APK 2022 For Free.
Wifiphisher Requirements
- Working Linux system, most preferably Kali Linux. Users have tried making it work on various distros, but this is the only officially supported distribution.
- Wireless network adaptor that can support AP and monitor mode and also can injection. Keep in mind that the drivers must support Netlink.
Alternative Choices
Wifiphisher Download 2022 – Free Rogue Access Point Framework
If you ever wanted to test Man in the Middle Attacks on your wireless network, then Wifiphisher free download is the best framework to do so! This article covers installation and how to use it too! You can also read the official documentation too to get a deeper understanding of how this tool works.
Build: 1.4 (Latest Version).






